Packages
14 Days
FREE TRIAL License
- Full Cross-Referenced Access To:
- NIST SP 800-171 r1
- Full Cross-Referenced Access To:NIST SP 800-171 r1NIST SP 53-r4
- NIST Cybersecurity Framework
- *No Credit Card Required
Billed Annually
Individual Business License
- Full Cross-Referenced Access To:
- NIST SP 800-171 r1
- NIST SP 53-r4
- NIST Cybersecurity Framework
- Best Practices
- Customizable Templates
- Compliance & Remediation Notation
- Artifact Attachment/Upload
- Unlimited Users & Access
- Email Support
- Contact Us for Technical Support Pricing
Coming Soon
Enterprise License
- Full Cross-Referenced Access To:
- NIST SP 800-171 r1
- NIST SP 53-r4
- NIST Cybersecurity Framework
- Best Practices
- Customizable Templates
- Compliance & Remediation Notation
- Artifact Attachment/Upload
- Unlimited Users & Access
- Email Support
- Contact Us for Technical Support Pricing
- Cybersecurity Maturity Model Certification (CMMC) Coming Soon!
The DASHBOARD
YOUR FOUNDATION FOR IMPROVING SECURITY POSTURE OVER TIME
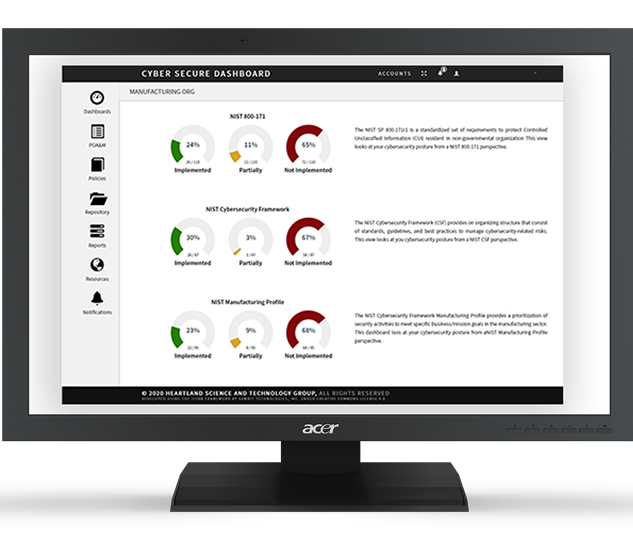
“One-and-Done” Excel-ware and Checklists Just Aren’t Enough
Manage the Cybersecurity Lifecycle
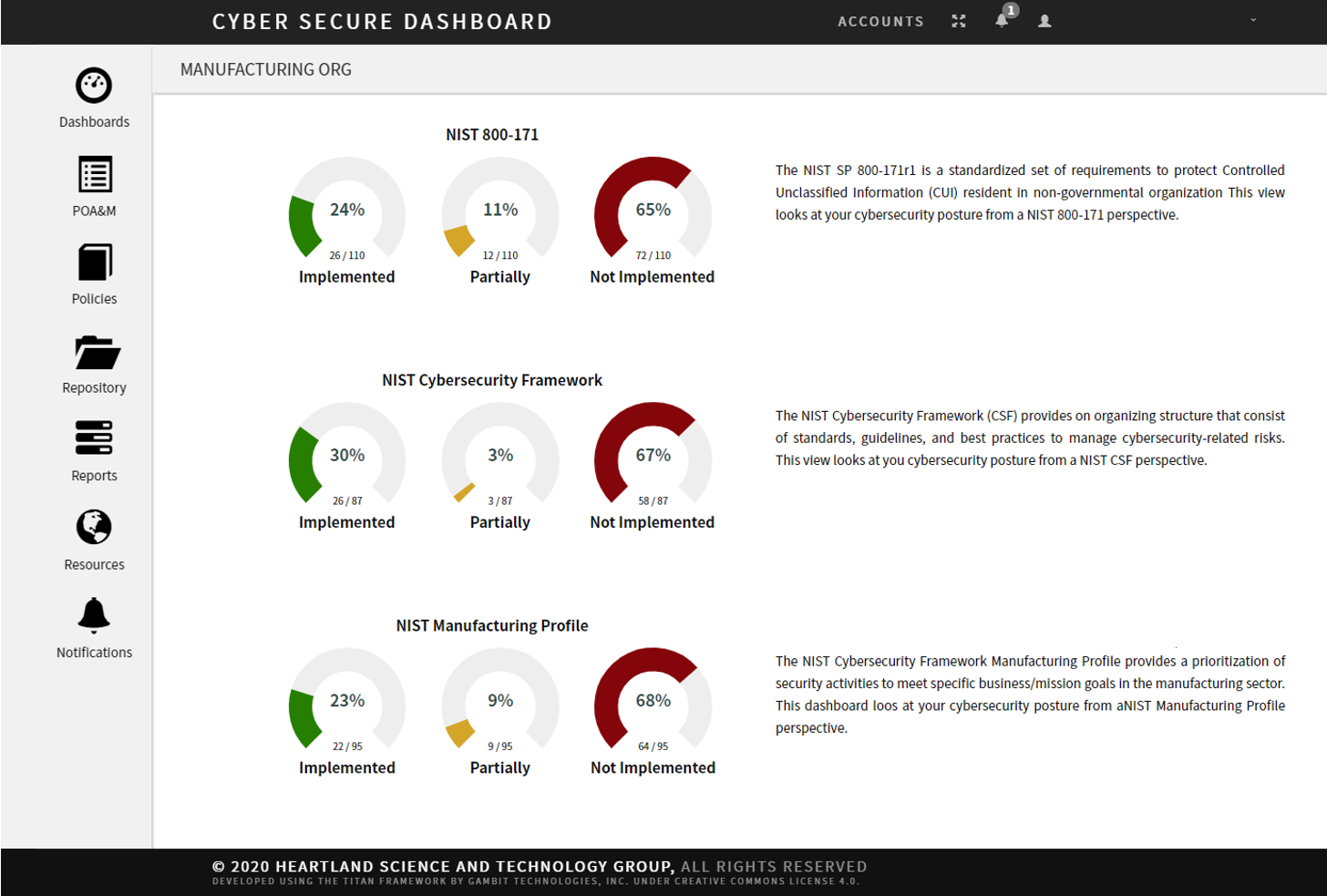
The Cyber Secure Dashboard is a management tool designed to speed initial assessment, clarify and prioritize requirements, and integrate knowledge from your entire security operation into a single, easy to navigate tool. It cross-references multiple DoD mandated control requirements and risk management standards.
The Dashboard provides best-practices and expert implementation guidance, combined with an innovative "learn-by-doing" approach to compliance. Intuitive, and easy to navigate, the Dashboard facilitates greater enterprise-wide cybersecurity awareness by making the process more understandable and accessible to all internal stakeholders: IT, Security, HR, Contracts Managers and Executives. It supports the sharing and vetting of an organization's cybersecurity posture with external stakeholders and trusted third parties: IT Service Providers, Security Consultants, Government Contracting Officers, Procurement Managers, Prime Contractors or Insurance Providers.
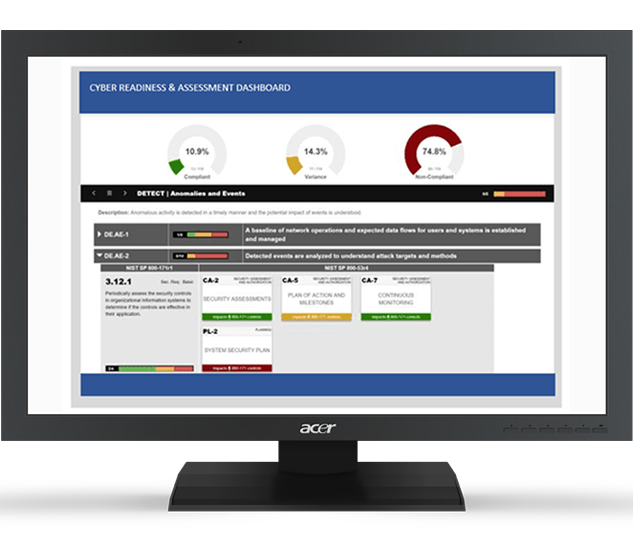
A Tool to Streamline Compliance and Improve Risk Management
We Keep You Current As the Standards Evolve
Even the most experienced Information Technology (IT) professionals find it challenging to comply with the NIST cybersecurity controls. The process requires sifting through numerous, obscure cybersecurity documents, standards, and controls while attempting to develop solutions that are tailored to each individual organization’s needs — a process further complicated by continually changing regulations and contractual agreements.
The Cyber Secure Dashboard overcomes these challenges by intuitively guiding the organization through the process of securing their information technology systems. The Dashboard provides detailed, step-by-step instructions, in-tool documentation written by our own security experts, industry best practices, customizable document templates, links to curated external reference materials – as well as a central repository for documentation and 3rd party validation
9+ Customizable Policy Templates to Speed Compliance
Writing cyber security policies from scratch can take hundreds of hours. Customers say that our cost-saving customizable templates are worth the entire price of an annual license.
- Information Security Policy
- IT Business Continuity – Backup Recovery Policy
- POAM – Plan of Action and Milestones
- Incident Reporting and Data Breach Response Policy
- Acceptable Use Policy
- Information Security Program
- HR Personnel Security Management Policy
- Technical Controls Policy
- Security Operations Policy

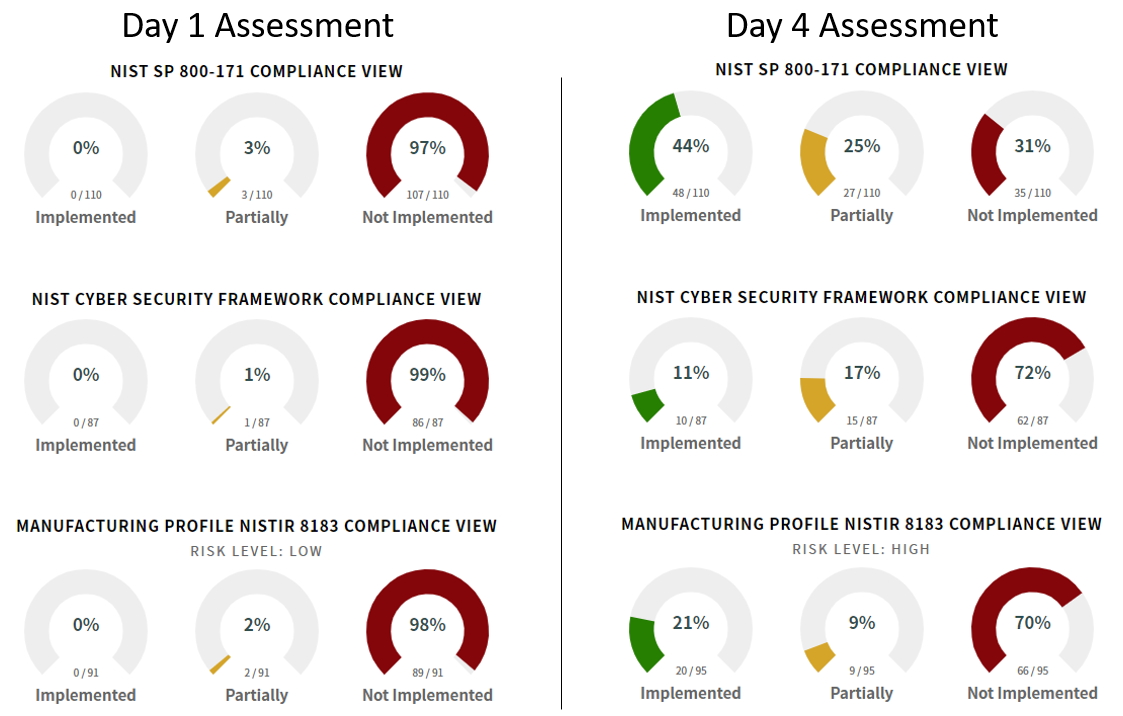
Faster Initial Assessment and POAM Using Our Step-By-Step Process
Speed initial assessment by accessing our in-tool supplemental guidance -- best practices written by our industry cyber security experts.
- Remove the guesswork
- Significantly improve your security posture
- Save time
- Establish a baseline Plan of Action and Milestones (POAM)
- Visually track compliance activity and efforts over time
Individual Business or Entire Supply Chain
Primes, Subs and Security Consultants
Individual businesses will find the Cyber Secure Dashboard useful for managing the complex process of compliance. Many businesses are struggling - and even now efforts are underway to create a new CMMC certification -- adding an auditing component to the existing DFARS requirements. The Dashboard will provide a seamless transition as federal requirements continue to shift over time.Enterprise Awareness
Long-Term Security and Improved Communication
Cybersecure Dashboard provides tools and templates to implement, manage, and communicate cybersecurity requirements to your entire enterprise: Security Officers, Engineers, Program Managers, Developers, Users, HR and C-Suite Executives.Support Supply Chain Compliance with a Prime Contractor License
The Cyber Secure Dashboard supports Prime Contractors and Subs - improving the cybersecurity posture of every business up and down the entire federal supply chain.
- Seamlessly transition from NIST 800-171 to the New CMMC Standard (Coming Soon)
- Support for Dispersed Businesses or Multiple Business Units Required to Meet Different Standards
- Gather Insights to Reliably Inform Supply Chain Disruption Contingency Planning
- Support Existing Subs Struggling To Meet Compliance Requirements
- Improve Overall Supply Chain Security
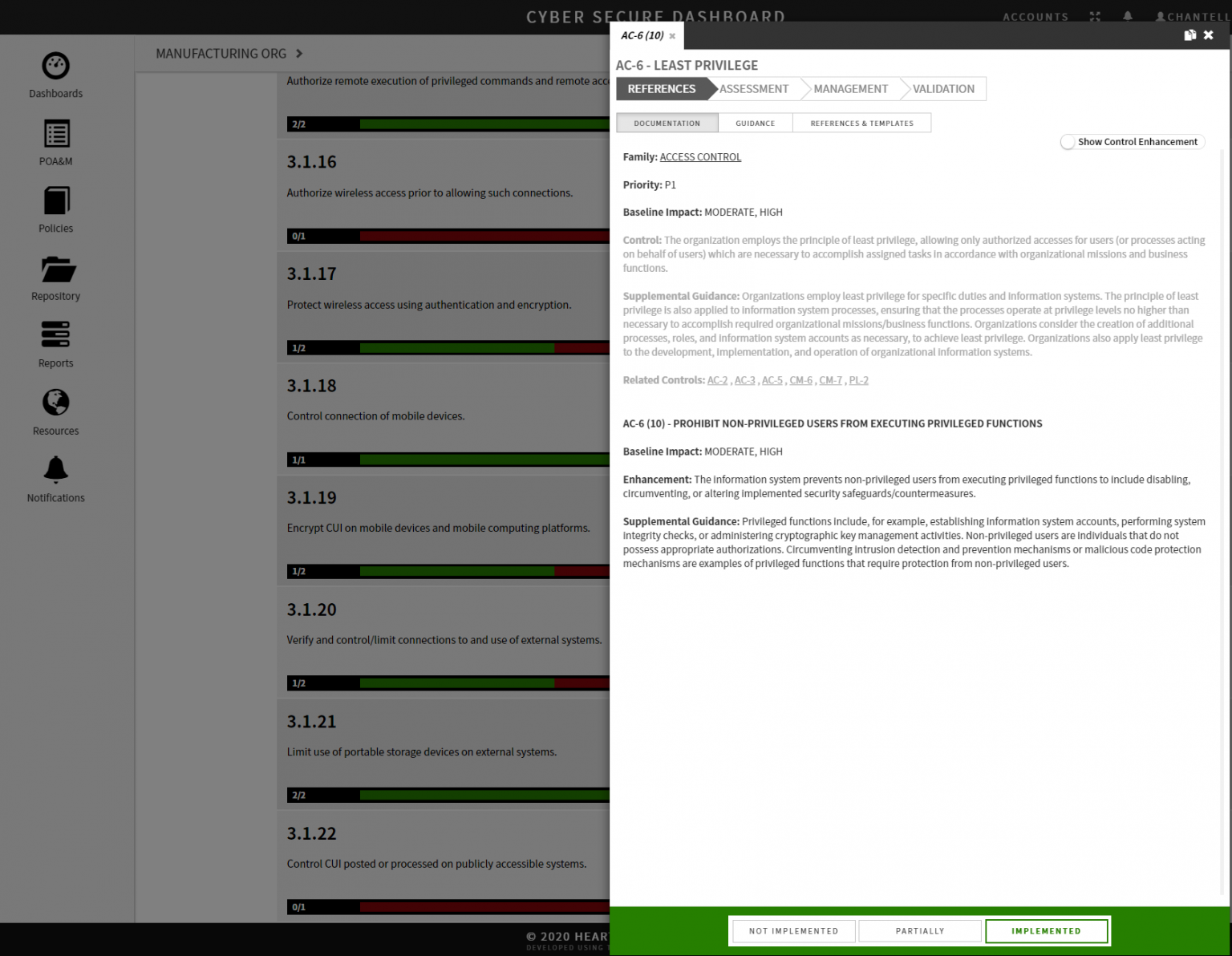
Enterprise License For IT and Security Consulting Firms
The Cyber Secure Dashboard supports Security and IT Consulting - providing management tools for easy consulting and collaboration
- Reports with Easy To Understand Graphics Showing Ongoing Progress
- Guide Clients Through Audits
- Seamlessly Transition Clients from NIST 800-171 to CMMC With No Lost Time or Effort
- Explanations in Plain Language Facilitate Client Education
- Discount – Savings Can Be Passed to Clients or Built-In To Fees

You Aren't Alone...
The Journey Starts Here
Meeting initial requirements is challenging. But it’s only the beginning of the journey. Requirements will inevitably evolve. The Dashboard will position your business to achieve compliance now and maintain compliance in the future.
Guidance
We demystify complex and vague requirements. As you work your way through each control we provide expert advice
best practices and direct links to carefully curated external resources — clarity where and when you need it.
Avoid Costly Errors
Mistakes could disqualify you from doing business with the Department of Defense — you need to establish sound cyber security processes and position your company to meet evolving compliance requirements and standards.
Ready to Get Started?
Subscriptions – Annual subscriptions will begin on the day of purchase and will automatically renew each year on the same date. If at any time you wish to cancel your subscription, you may do so by contacting Iviry. Email support@iviry.com
Refund/Cancellation Policy – You may cancel your subscription at any time. However, Iviry does not offer refunds on Subscription products after the 14 Day Trial has ended.
Privacy/Personally Identifiable Information Policy – Iviry contracts with online payment service provider, Authorize.net. Authorize.net, manages all payments and associated card user data on our behalf. We do not access or save any credit card user information – Authorize.net provides us a secure token which is then associated with a Cyber Secure Dashboard User account. To read more about our policy regarding user generated content or user information provided to us through our user registration process, see our Terms and Conditions.
Cyber Secure Dashboard
Built and Supported Through Collaboration Across Trusted Public and Private Entities
A Sound Investment in Risk Management
Enter Data Once. View It Through the Lens of Multiple Standards Over Time.
The Office of the Assistant Secretary of Defense for Acquisition is creating the Cybersecurity Maturity Model Certification (CMMC) – a new cybersecurity standard.
This standard is anticipated to be implemented in mid-2020 and the Dashboard team is working to roll-out the new CMMC view very soon.
For more information on the CMMC, visit our FAQ.
This publication has been developed by NIST to further its statutory responsibilities under the Federal Information Security Modernization Act (FISMA) of 2014, 44 U.S.C. § 3551 et seq., Public Law (P.L.) 113-283. NIST is responsible for developing information security standards and guidelines, including minimum requirements for federal information systems, but such standards and guidelines shall not apply to national security systems without the express approval of appropriate federal officials exercising policy authority over such systems. This guideline is consistent with the requirements of the Office of Management and Budget (OMB) Circular A130.
This publication provides federal agencies with a set of recommended security requirements for protecting the confidentiality of Controlled Unclassified Information (CUI) when such information is resident in nonfederal systems and organizations; when the nonfederal organization is not collecting or maintaining information on behalf of a federal agency or using or operating a system on behalf of an agency; and where there are no specific safeguarding requirements for protecting the confidentiality of CUI prescribed by the authorizing law, regulation, or governmentwide policy for the CUI category or subcategory listed in the CUI Registry. The security requirements apply to all components of nonfederal systems and organizations that process, store, or transmit CUI, or that provide security protection for such components. The requirements are intended for use by federal agencies in contractual vehicles or other agreements established between those agencies and nonfederal organizations.
NIST SP 800-53 is a publication that was developed by NIST to further its statutory responsibilities under the Federal Information Security Management Act (FISMA), Public Law (P.L.) 107-347. NIST is responsible for developing information security standards and guidelines, including minimum requirements for federal information systems, but such standards and guidelines shall not apply to national security systems without the express approval of appropriate federal officials exercising policy authority over such systems.
It provides a catalog of security and privacy controls for federal information systems and organizations and a process for selecting controls to protect organizational operations (including mission, functions, image, and reputation), organizational assets, individuals, other organizations, and the Nation from a diverse set of threats including hostile cyber attacks, natural disasters, structural failures, and human errors.
The NIST Cybersecurity Framework was created through collaboration between government and the private sector. It uses a common language to address and manage cybersecurity risk in a cost-effective way based on business needs without placing additional regulatory requirements on businesses. The Framework focuses on using business drivers to guide cybersecurity activities and considering cybersecurity risks as part of the organization’s risk management processes. The Framework consists of three parts: the Framework Core, the Framework Profile, and the Framework Implementation Tiers. Each Framework component reinforces the connection between business drivers and 188 cybersecurity activities.
The Dashboard provides support for the NIST Manufacturing Profile, a part of the Cybersecurity Framework. The Manufacturing Profile can be used as a roadmap for reducing cybersecurity risk for manufacturers — aligning with manufacturing sector goals and industry best practices. It provides a voluntary, risk-based approach for managing cybersecurity activities and reducing cyber risk to manufacturing systems. The Manufacturing Profile is meant to enhance but not replace current cybersecurity standards and industry guidelines that the manufacturer is embracing.
Standards Under Development
Cybersecurity Maturity Model Certification (CMMC)
The Cyber Secure Dashboard Team is always working to expand offerings and improve — if you have specific needs that we haven’t met, please get in touch.




